Software as a Service (SaaS) refers to applications that are hosted remotely. You access them through the Internet without needing to download software. It simplifies work and does so quickly using tools like Google Workspace or Slack.
Cloud security risks involve potential threats, vulnerabilities, and exposures that come with using cloud-based services. In the age of SaaS, these risks take new forms: different control models, shared responsibility, rapid deployment, and decentralized usage.
SaaS applications are increasingly important in today’s business activities. However, despite their advantages, using SaaS introduces significant cloud security. A recent survey by the Cloud Security Alliance (CSA) shows that 63% of organizations detect external data oversharing, and 55% report that employees use SaaS without security’s involvement.
However, SaaS brings new challenges. Many teams use hundreds of apps. This growth creates cloud security that are hard to spot. As a result, breaches happen often.
By 2026, most companies will face cloud security related to SaaS. Reports indicate that 99% of cloud failures are caused by customer mistakes. Misconfigurations are the leading issue, and shadow IT adds many hidden dangers.
Why this matters:
With SaaS apps, your information and activities do not always have any physical control. That means you must think differently about protection. Many organisations assume the cloud provider handles everything — but in practice your team still holds responsibility for many facets. That gap is where cloud security tend to hide.
Why SaaS Security is Uniquely Challenging
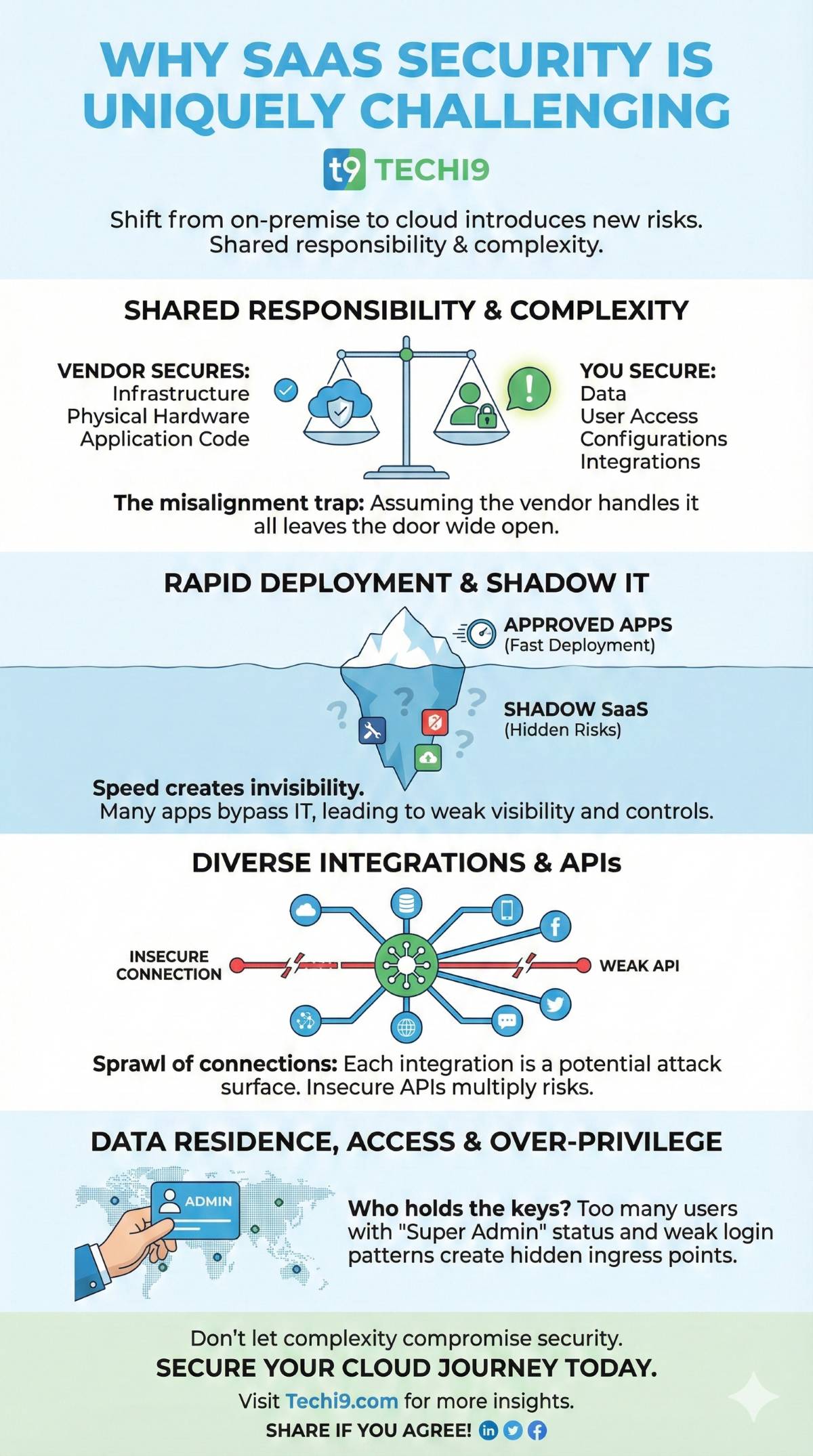
Shared responsibility and complexity
In traditional IT you might host everything yourself. With SaaS the vendor hosts the application, but you still manage access, data usage, configurations and integrations. The concept of cloud security shows up via mis‐aligned responsibilities. The vendor secures infrastructure; you secure data, users and settings.
Rapid deployment and shadow IT
SaaS enables fast deployment — that speed is great. However, it also means many applications can bypass the IT/security teams (so called “shadow SaaS”). That leads to weak visibility, weak controls and hidden cloud security.
Diverse integrations and APIs
SaaS apps often plug into other systems, cloud services and APIs. Each connection is a potential attack surface. Weak API controls or insecure integrations multiply the cloud security.
Data residence, access and over-privilege
When data is in the cloud, who can access it? Are permissions tight? Are audit logs active? Many organisations find that user accounts are over-privileged or login patterns are weak, creating hidden ingress points. These are real cloud security.
Hidden Blind Spots in SaaS Environments
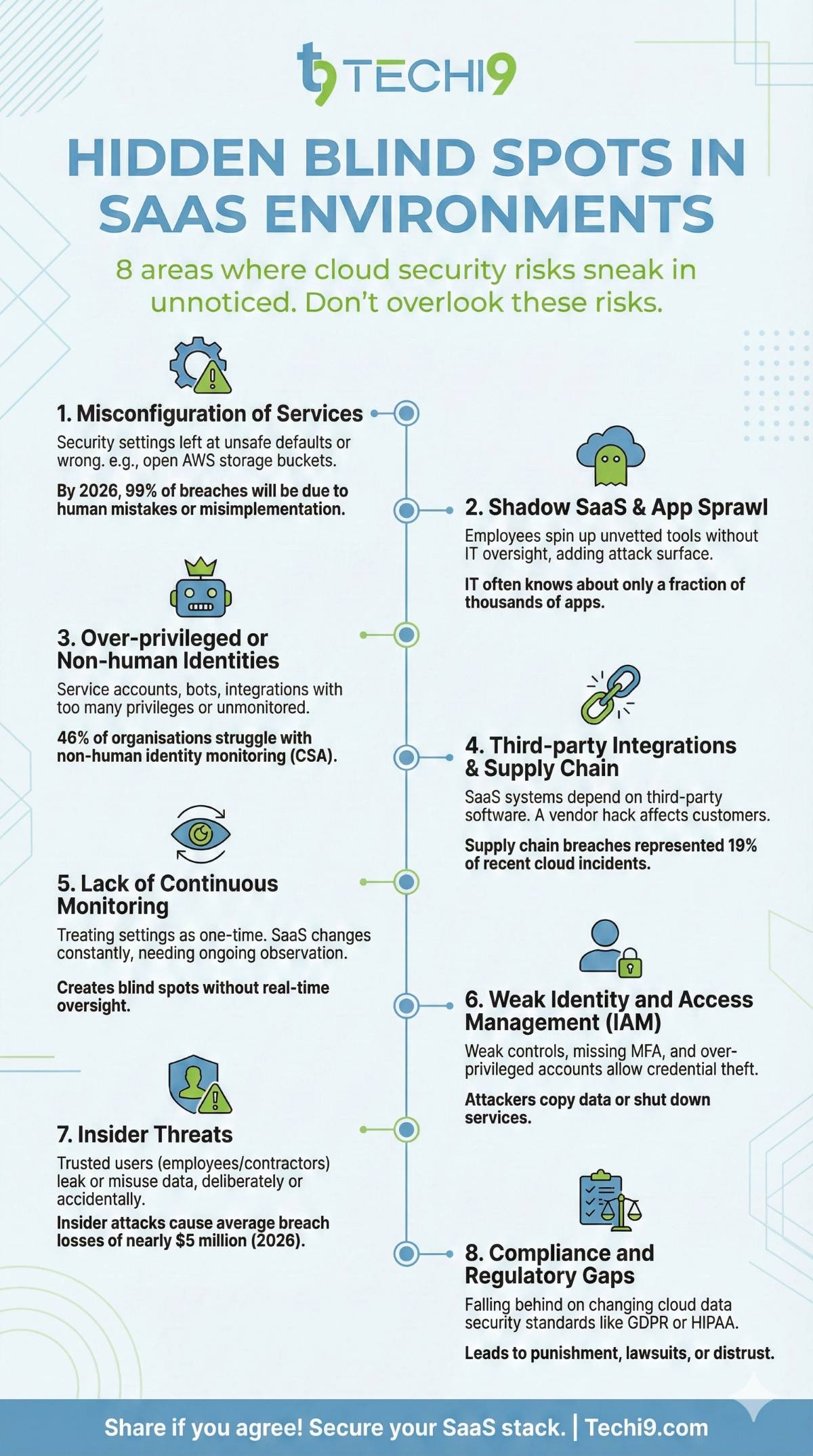
There are several areas where cloud security sneak in unnoticed. For SaaS companies, these blind spots can be costly. Here are specific places where organisation’s overlook risks:
Misconfiguration of services
Misconfiguration means security settings are set up wrong or left at unsafe defaults. Indicatively, a person can leave an AWS storage bucket in an open state. By 2026, 99% of cloud security breaches will be due to human mistakes or misimplementation.
One attack may sometimes leak out millions of records or confidential user information. Automated deployment tools and rapid updates make these errors more likely.
Shadow SaaS and uncontrolled app sprawl
Employees may spin up SaaS tools without IT oversight. These unvetted tools add to the attack surface and make governance of cloud security harder. Shadow IT happens when employees use cloud apps and store data beyond IT’s knowledge. SaaS companies often run thousands of apps, but IT teams know about only some of them.
Over-privileged or non-human identities
Many SaaS platforms have service-accounts, bots, integrations. If these identities have too many privileges or are unmonitored, they become a blind spot. The CSA found 46% of organisations struggle with non-human identity monitoring.
Third-party integrations and supply chain risk
This is a classic cloud security scenario. Many SaaS systems depend on third-party software or integrations. If one vendor gets hacked, it can affect all customers. Supply chain breaches represented 19% of cloud incidents recently.
Lack of continuous monitoring and posture management
Many organisations treat settings as a one‐time activity rather than ongoing. However, SaaS is always changing, and when continuous observation is not practiced, it creates blind spots.
identity and access management iam (IAM)
The attackers can steal, guess or abuse the user credentials, in case the identity controls are weak. Credential theft can let attackers copy data or shut down services. Multi-factor authentication (MFA) helps, but sometimes it’s missing. Over-privileged accounts also create risks, as employees may have more access than needed.
Insider Threats
Insider threats are caused by trusted users — like employees or contractors — who leak or misuse data. These may be deliberate or accidental. In 2026, insider attacks have caused average breach losses of nearly $5 million.
Since insider actions can look normal, it is hard to detect problems without advanced monitoring.
Compliance and Regulatory Gaps
With cloud data security standards (such as GDPR or HIPAA), it is a simple matter to be left behind by the change of rules. The inability to satisfy necessities may lead to punishment, lawsuits, or distrust.
How to Address Cloud Security Risks in SaaS
Now the practical bit. These risks can be minimized by following the steps below.
Create good governance and an inventory
- Begin by listing all SaaS applications in operation (non-IT operations, too).
- Identify the owner of each service, who sets it up, and what data it contains.
- Use this baseline so you can monitor change and scope risks.
This helps identify hidden cloud security, such as unapproved apps or uncontrolled data flows.
Apply strong access management
- Implement multi-factor authentication (MFA) for users.
- Use the least-privileged access: users are only supposed to have access to what is required of them, at the right time.
- Review service/bot accounts: reduce privileges, apply separate credentials, monitor usage.
These steps mitigate risks like account hijacking and internal misuse.
Secure configurations and enable automation
- Ensure default settings are secured (i.e opportunity to open sharing, allow public opening).
- Once misconfigurations are checked continuously using automation, or with the help of tools such as SSPM (SaaS Security Posture Management).
- Articulate Baselines of configuration and monitor deviations.
Monitor integrations, APIs, and data flows
- Map how your SaaS apps integrate with others and what APIs are exposed.
- Track API traffic, presence of anomalies, and unauthenticated connections.
- Data flows Audit data: In what SaaS apps does PII or sensitive data exist? Who can export it? These are key cloud security to track.
Enforce classification, encryption and data protection
- Categorize the information according to the degree of sensitivity and encrypt high-risk information at rest and in transit.
- Control export or download of sensitive content.
- Implement PLS tools of DLP (data loss prevention) tools in SaaS devices.
Implement frequent audits, educate, and prepare for threats.
- Audits are to include vendor and internal audit: what controls are provided by the SaaS vendor, and are properly configured?
- Workers need to get training on the risks of using clouds safely, SaaS, and shadow IT.
- Have existing incident response plans /what to do in case of a SaaS breach: who to call, how to isolate, how to notify.
Selection of vendors and SLAs
- The aspects that should be considered when selecting a provider of SaaS include their security features, certifications (i.e., ISO 27001, SOC 2), and how they carry out vendor integrations.
- The contractual roles, responsibilities, and accountability for security should be stipulated. This reduces a number of latent cloud security risks.
Latest Cloud Security Threats in 2026
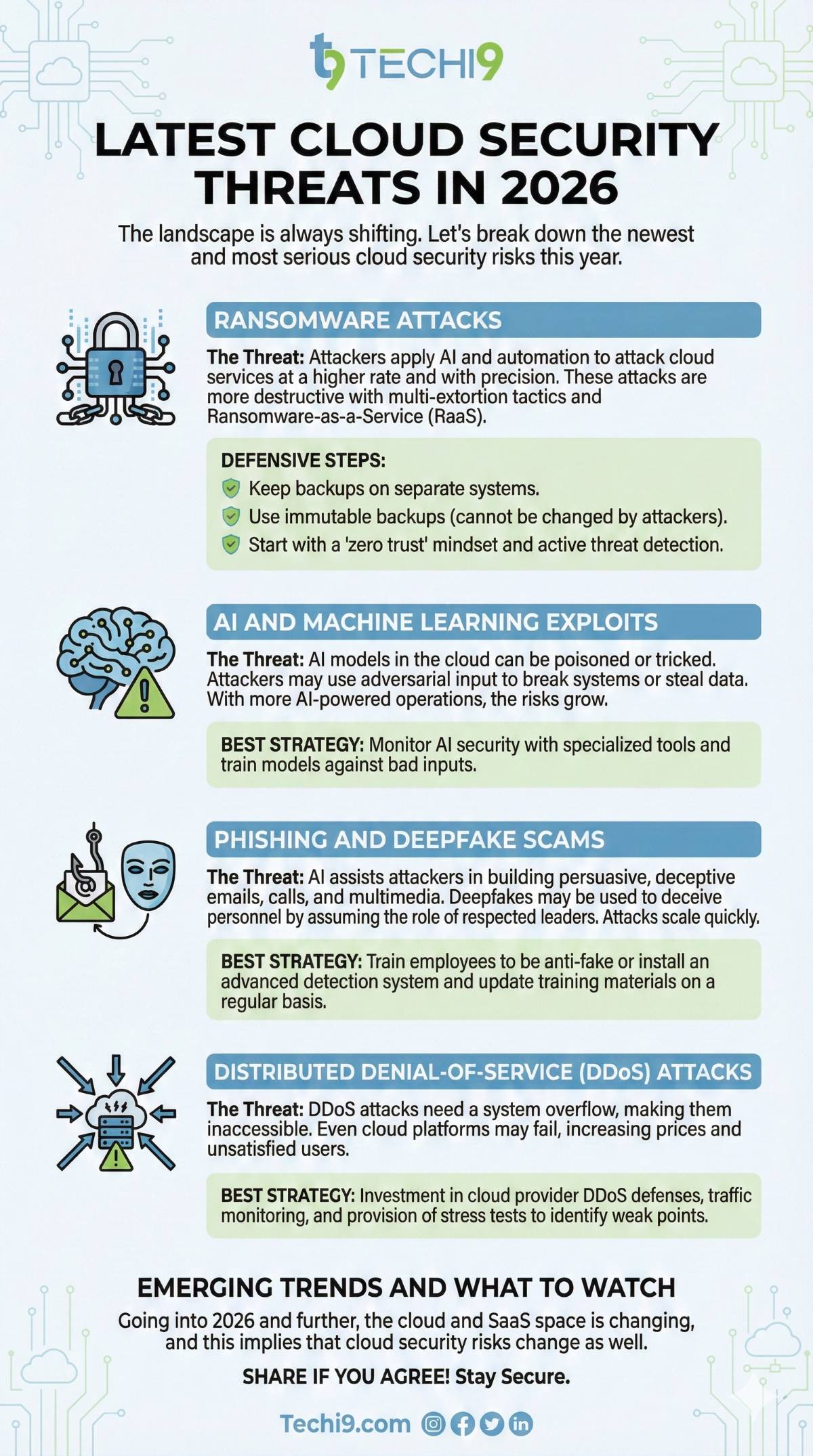
The landscape is always shifting. Let’s break down the newest and most serious cloud security risks this year.
Ransomware Attacks
Ransomware locks valuable data or systems until payment. In the year 2026, attackers apply AI and automation to attack cloud services at a higher rate and with precision. These attacks are more destructive with the help of multi-extortion tactics and Ransomware-as-a-Service (RaaS).
Defensive Steps:
- Keep backups on separate systems.
- Use immutable backups (cannot be changed by attackers).
- Start with a “zero trust” mindset and active threat detection.
AI and Machine Learning Exploits
AI models in the cloud can be poisoned or tricked. Attackers may use adversarial input to break systems or steal data. With more AI-powered operations, the risks grow.
Best Strategy: Monitor AI security with specialized tools and train models against bad inputs.
Phishing and Deepfake Scams
AI assists attackers in building persuasive, deceptive emails, calls, and multimedia. Deepfakes may be used to deceive personnel by assuming the role of respected leaders. Attacks scale quickly.
Best Strategy: Train employees to be anti-fake or install an advanced detection system and update training materials on a regular basis.
Distributed Denial-of-Service (DDoS) Attacks
DDoS attacks need a system overflow, making them inaccessible. Even the cloud platforms may fail, increasing prices and unsatisfied users.
Best Strategy: Investment in cloud provider DDoS defenses, traffic monitoring, and provision of stress tests to identify weak points.
Emerging Trends and What to Watch
Going into 2026 and further, the cloud and SaaS space is changing, and this implies that cloud security risks change as well.
For example:
- The CSA’s 2026 report finds that 76% of organisations are increasing budgets for SaaS security, but many still rely on manual or fragmented tools.
- Non-human identities (bots, AI agents) and SaaS-to-SaaS integrations are increasingly common — and they expand the attack surface.
- Zero-trust models and continuous compliance monitoring are becoming default for SaaS environments.
- With more remote work, more devices, more integrations, the speed of change keeps accelerating — which means static security will no longer suffice.
Proven Strategies to Address Cloud Security Issues
We will continue by talking about viable methods of alleviating cloud security risks in SaaS. The strategies help in safeguarding the information, reputation, and ensuring that the users are ultimately satisfied.
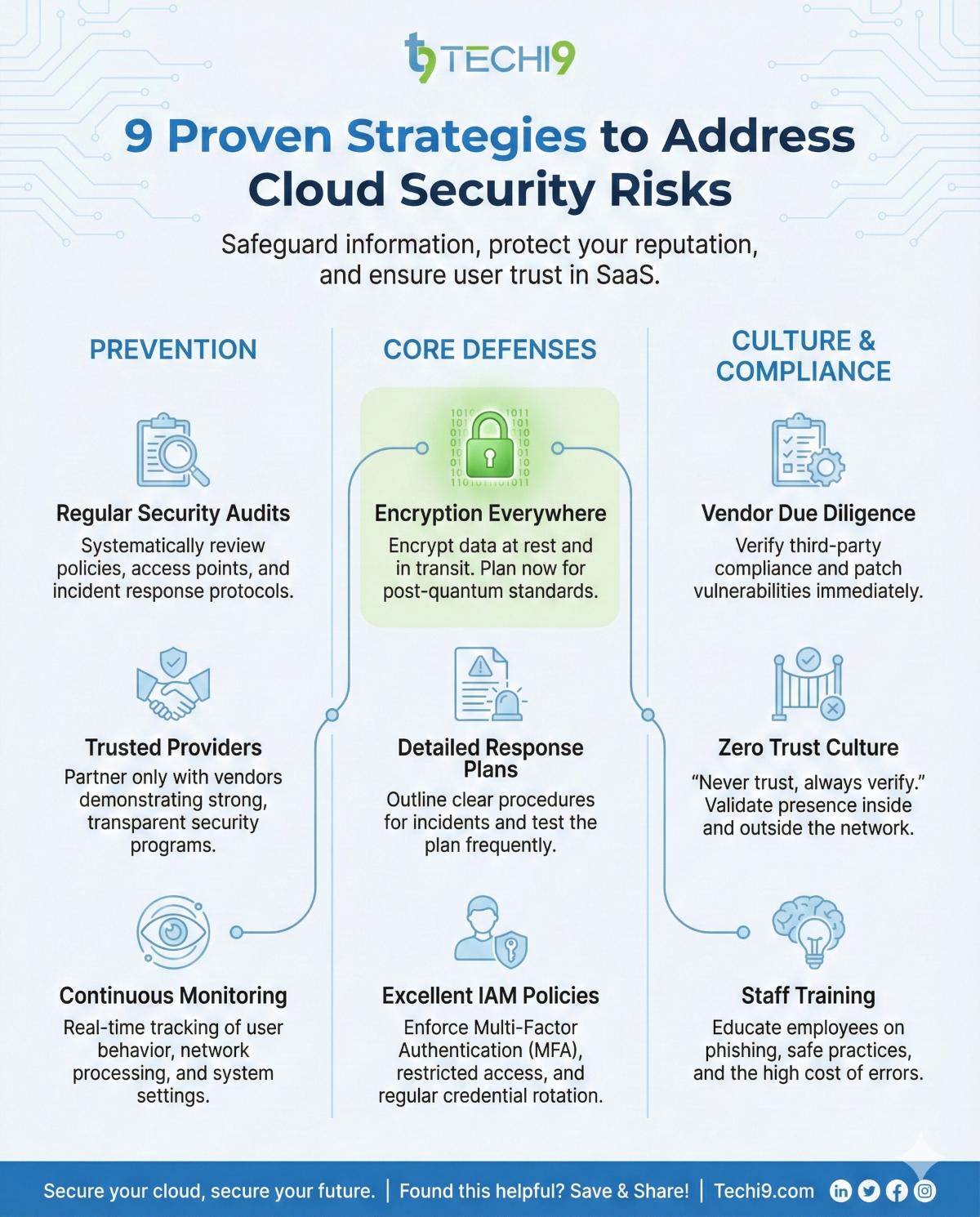
- Regular Security Audits: Systematically review policies, access points, and responses.
- Trusted Providers: Work with vendors that have strong, transparent security programs.
- Continuous Monitoring: Check at all times the behavior of the users, network processing, and system settings.
- Encryption Everywhere: Encrypt resting data and transfer data; plan to move to post-quantum standards.
- Detailed Response Plans: Outline clear procedures for incidents; test the plan often.
- Excellent IAM Policies: Use restricted user access, MFA, and change credentials.
- Vendor Due Diligence: Check the compliance of all the third-party vendors, and Patch vulnerabilities quickly.
- Zero Trust Culture: Do not trust the users of the network or the equipment per se, verify their presence inside and outside the network.
- Staff Training: Educate the employees on phishing, safe practices, and the price of errors.
How to Address cloud security strategy
Fixing cloud security risks is straightforward. Start with basics. Build from there.
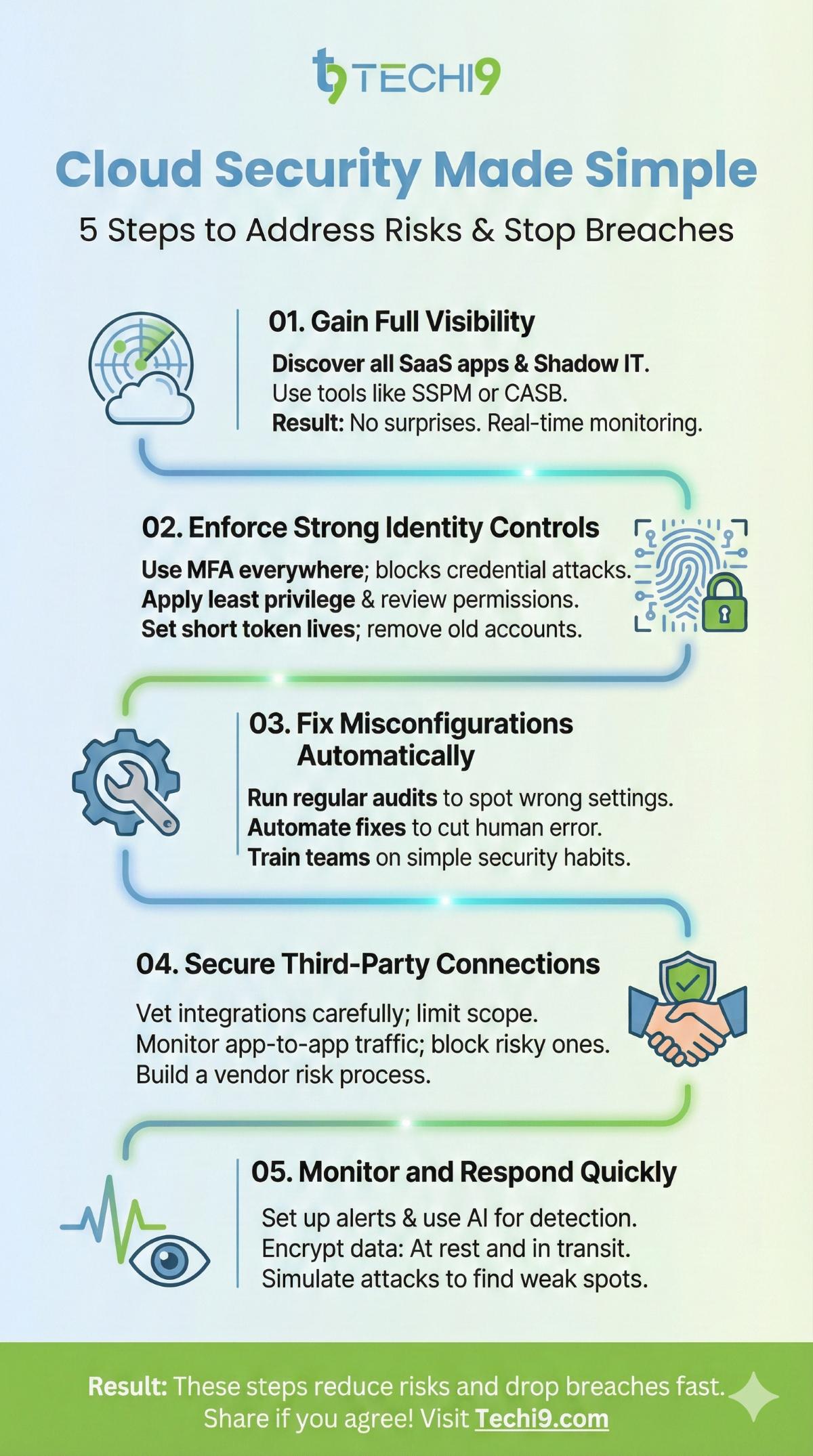
Step 1: Gain Full Visibility
- First, discover all SaaS apps in use. Tools like SSPM or CASB help.
- They scan for shadow IT. You see every app and user.
- As a result, no more surprises. Monitor activity in real time.
Step 2: Enforce Strong Identity Controls
- Use MFA everywhere. It blocks most credential attacks.
- Next, apply the least privilege. Give access only when needed.
- Review permissions often. Remove old accounts fast.
- For tokens, set short lives. Monitor their use.
Step 3: Fix Misconfigurations Automatically
- Run regular audits. Tools spot wrong settings quickly.
- Automate fixes where possible. This cuts human errors.
- Train teams too. Simple habits prevent big cloud security risks.
Step 4: Secure Third-Party Connections
- Vet integrations carefully. Limit their scope.
- Use tools to watch app-to-app traffic. Block risky ones.
- Build a vendor risk process. Check partners regularly.
Step 5: Monitor and Respond Quickly
- Set up alerts for odd actions. Use AI for better detection.
- Log everything. This helps investigations.
- Test your setup often. Simulate attacks to find weak spots.
- Additionally, encrypt data always. At rest and in transit.
- Follow shared responsibility. Know your part clearly.
These steps reduce cloud security risks a lot. Many companies see breaches drop fast.
Best Tools to Fight Cloud Security Risks
Good tools make fixes easy. Here are top ones for 2026.
- SSPM tools: Check SaaS postures. Fix configs auto.
- CASB: Control cloud traffic. Block threats.
- DSPM: Track sensitive data. Spot leaks.
- CNAPP: Full cloud protection. Covers SaaS too.
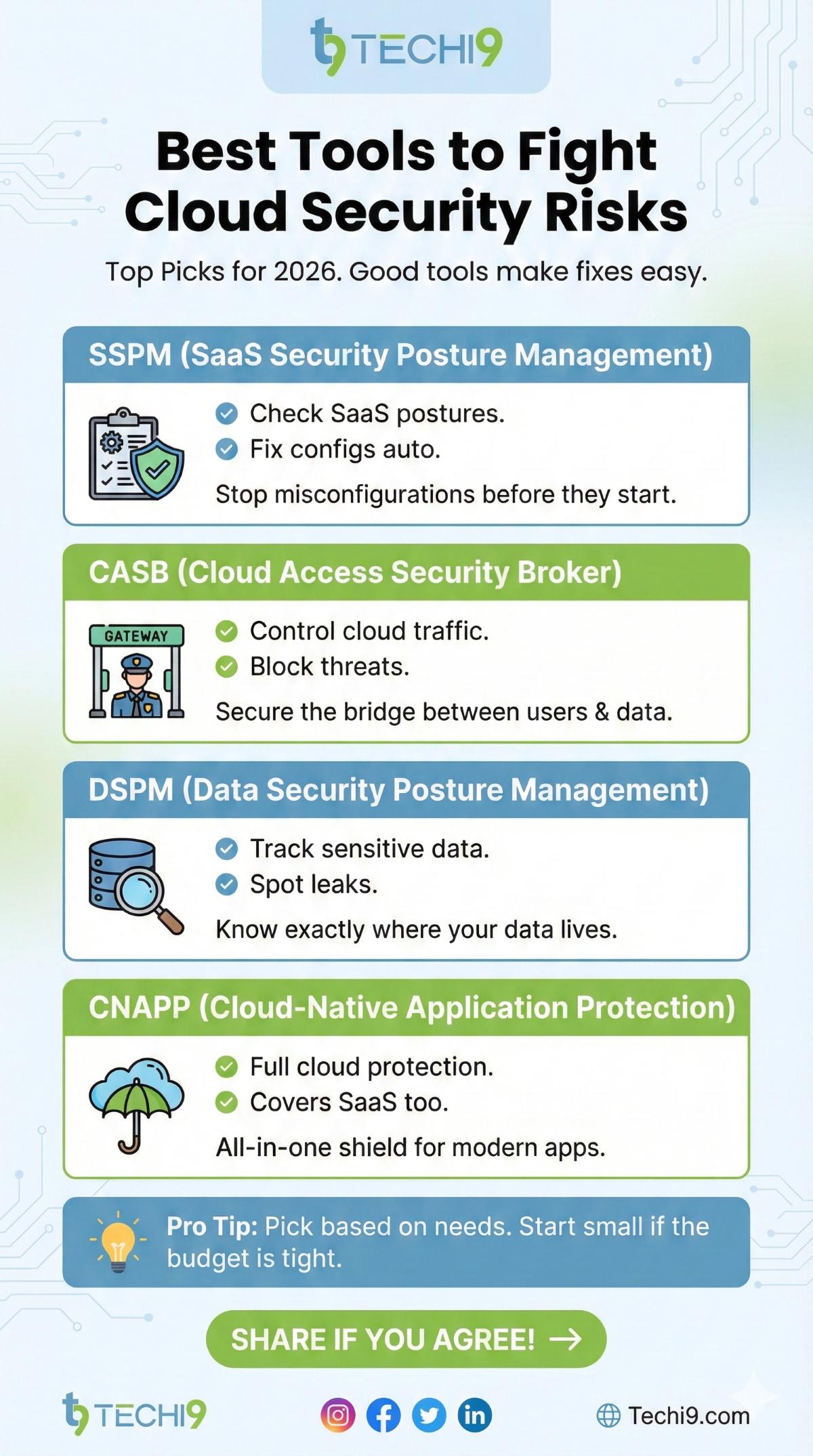
Pick based on needs. Start small if the budget is tight.
The Future of SaaS and Cloud Security
The security issue will continue to increase as cloud technology advances and hackers employ more intelligent strategies. Increased companies will use AI-driven security measures and automation as a defense of their data. Meanwhile, compliance will take a new form as new laws will force businesses to remain adaptable and nimble.
The most effective SaaS organizations will strike a balance between rapid innovation and an extreme level of security. Frequent risk evaluations, great alliances, and lifelong learning ensure businesses are ahead of attackers.
FAQ: Top Cloud Security Risks in SaaS (2026)
What are the security risks of the cloud?
Data breaches
Loss of control over data
Insecure APIs
Account hijacking
Insider threats
Inadequate cyber security measures
Compliance violations
Data loss
Service outages
Denial of service attacks
What are the top 5 cyber security risks?
Phishing Attacks
Ransomware
Insider Threats
Malware
Distributed Denial of Service (DDoS)
What are the 4 C’s of cloud security?
The 4 C’s of cloud security are:
Confidentiality
Integrity
Availability
Compliance
What are the top 5 cloud computing security challenges?
Data Breaches
Insecure APIs
Account Hijacking
Data Loss
Compliance Violations
Final Thoughts
It is impossible to turn a tide of SaaS and cloud-related work. That comes with flexibility and efficiency – yet it comes at a cost of cloud security risks that remain unknown, dynamic, and underestimated. Their one trick is not to consider SaaS like the traditional on-premises software. Better said, think in layers; governance, access, data, integrations, Everlasting checking.
By doing so you’ll not just plug obvious holes, you’ll uncover the hidden blind spots. Moreover, you’ll build a posture that scales as your SaaS footprint grows.
Don’t wait for the breach to force change. Start today.
